Authentication software is designed to verify user identities before granting access to systems, applications, and networks. It plays a critical role in cybersecurity by preventing unauthorized access and securing sensitive information. Over time, authentication has evolved from simple password-based logins to sophisticated multi-factor authentication (MFA), biometric verification, and adaptive security models.
Popular authentication software includes Okta, Microsoft Entra ID (formerly Azure AD), Duo Security, Ping Identity, and Auth0. These solutions help businesses implement secure authentication methods while ensuring compliance with industry regulations. Related software categories include Identity and Access Management (IAM) software, Zero Trust Security software, and Privileged Access Management (PAM) software.

Okta – A cloud-based identity management service providing SSO, MFA, and adaptive authentication for businesses of all sizes.
Microsoft Entra ID (Azure AD) – Microsoft’s identity management solution with SSO, MFA, and integration with Microsoft 365 and Azure services.
Duo Security – A user-friendly MFA and zero-trust security platform that enhances login security for enterprises.
Ping Identity – An enterprise-grade authentication solution supporting SSO, adaptive authentication, and OAuth/OpenID.
Auth0 – A developer-friendly authentication and authorization platform with customizable authentication flows.
OneLogin – A cloud-based IAM solution that simplifies authentication through SSO and MFA.
RSA SecureID – A strong authentication tool using MFA and token-based security for enterprise environments.
Google Cloud Identity – Google’s identity and access management tool with SSO and multi-layer authentication.
IBM Security Verify – An AI-powered authentication and identity management platform.
CyberArk Identity – A security-focused authentication platform offering adaptive authentication and privileged access control.
The following table compares three leading authentication software solutions: Okta, Microsoft Entra ID, and Duo Security. These platforms offer robust authentication features, but their capabilities vary depending on business needs.
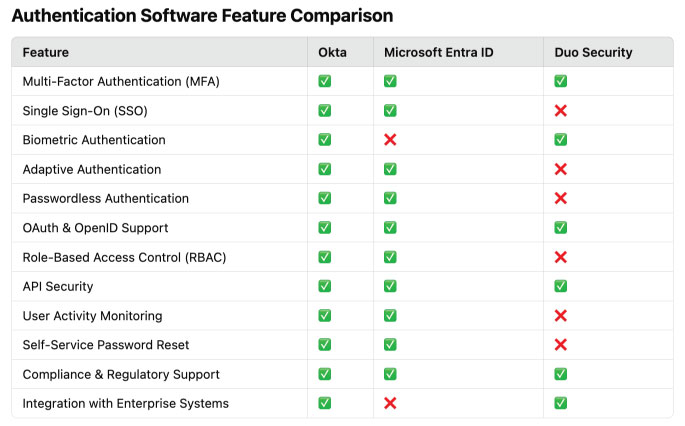
The feature comparison table highlights differences among Okta, Microsoft Entra ID, and Duo Security in authentication capabilities. Okta offers the most comprehensive feature set, including SSO, MFA, passwordless authentication, and adaptive authentication. Microsoft Entra ID provides strong enterprise integration and compliance support but lacks biometric authentication and full enterprise system integration. Duo Security focuses on MFA and API security but lacks features like SSO, adaptive authentication, and self-service password reset, making it more suited for organizations prioritizing multi-factor authentication over broader identity management.
Choosing the right authentication system for your app is crucial for securing user data while ensuring a smooth login experience. In this video, you’ll learn about different authentication methods, including password-based logins, multi-factor authentication (MFA), OAuth, and passwordless authentication, to help you decide which solution best fits your app’s needs. Whether you’re building a small web app or an enterprise-level platform, understanding how authentication software works will help you protect user identities, prevent security breaches, and improve user experience. Watch now to explore the best authentication options for your application!
This authentication software dashboard provides a centralized interface for managing user access, security settings, and login activity. At a glance, administrators can monitor recent login attempts, detect suspicious activity, and configure multi-factor authentication (MFA) settings. The dashboard includes visual graphs displaying authentication trends, along with real-time security alerts highlighting potential threats. Additionally, access control settings allow admins to enable or disable authentication features, enforce compliance policies, and integrate with third-party identity providers. With an intuitive layout and a sleek dark-themed UI, this dashboard enhances security management while ensuring a seamless user experience.

Authentication software incorporates a variety of security measures to ensure that only authorized users can access digital resources. From multi-factor authentication (MFA) to passwordless login, modern authentication solutions use advanced technologies to balance security and user convenience. Organizations also benefit from centralized identity management, risk-based authentication, and regulatory compliance tools to safeguard sensitive data.
Multi-Factor Authentication (MFA)
MFA enhances security by requiring users to verify their identity using multiple authentication factors, such as passwords, biometric data, or one-time passcodes. This approach significantly reduces the risk of credential theft and unauthorized access.
SSO simplifies user authentication by allowing access to multiple applications with a single set of credentials. This enhances user experience while reducing the burden of managing multiple passwords.
Biometric authentication leverages unique physical characteristics like fingerprints, facial recognition, or voice identification to verify users. This method enhances security while offering a frictionless login experience.
Adaptive authentication assesses real-time risk factors such as device type, location, and login behavior to determine authentication requirements. If an anomaly is detected, additional security steps may be triggered.
This feature eliminates traditional passwords by using biometrics, hardware security keys, or magic links for authentication. Passwordless login reduces the risk of phishing and credential-based attacks.
Authentication software supports OAuth and OpenID Connect to enable secure third-party authentication, allowing users to log in with existing credentials from services like Google or Facebook.
RBAC allows administrators to define user roles and assign access permissions accordingly. This ensures that users only have access to the resources necessary for their role.
APIs are commonly used for authentication processes in web and mobile applications. Authentication software protects API endpoints against unauthorized access, preventing data breaches.
Monitoring login attempts, failed authentications, and suspicious access patterns helps identify security threats. Detailed audit logs enhance visibility and regulatory compliance.
Users can reset their passwords without IT intervention, reducing support costs and improving productivity. This feature typically includes identity verification steps for added security.
Authentication solutions help organizations meet security standards such as GDPR, SOC 2, HIPAA, and PCI DSS by enforcing strong authentication policies and logging access attempts.
Modern authentication software integrates with cloud services, on-premise directories, and third-party identity providers to streamline user authentication across platforms.
Authentication software verifies user identities before granting access to systems, applications, or networks. It prevents unauthorized access and secures sensitive data.
Common types include password-based authentication, multi-factor authentication (MFA), biometric authentication, adaptive authentication, and passwordless authentication.
SSO reduces password fatigue, minimizes the risk of weak passwords, and centralizes access control, making authentication more secure.
Yes, passwordless authentication eliminates password-related vulnerabilities, reducing the risk of phishing and credential theft.
Adaptive authentication dynamically adjusts security requirements based on user behavior, location, and risk level.
Yes, most authentication solutions integrate with enterprise directories, cloud applications, and security frameworks.
Yes, authentication tools help organizations meet compliance standards like GDPR, SOC 2, HIPAA, and PCI DSS.
API authentication secures access to web services by verifying API requests using keys, tokens, or OAuth.
It uses unique physical traits like fingerprints or facial recognition to verify identity securely.
Popular choices include Okta, Microsoft Entra ID, and Ping Identity for their scalability and security.